Patching in the IoT Era: How Over-the-Air Updates Close Critical Security Gaps Faster
A single unpatched IoT device can compromise an entire corporate network – something nearly impossible to prevent manually. The solution? Over-the-Air updates. As the number of IoT devices is expected to exceed 32 billion by 2030 (source: Statista), the potential for security risks is growing exponentially. A well-known example is the Mirai botnet, which attempted to infect routers and surveillance cameras by exploiting default passwords and security vulnerabilities. It became infamous in 2016 when it disrupted major websites like Twitter, Netflix, and Dyn through large-scale DDoS attacks.
The Major Challenge – Why IoT Patching Is So Complex
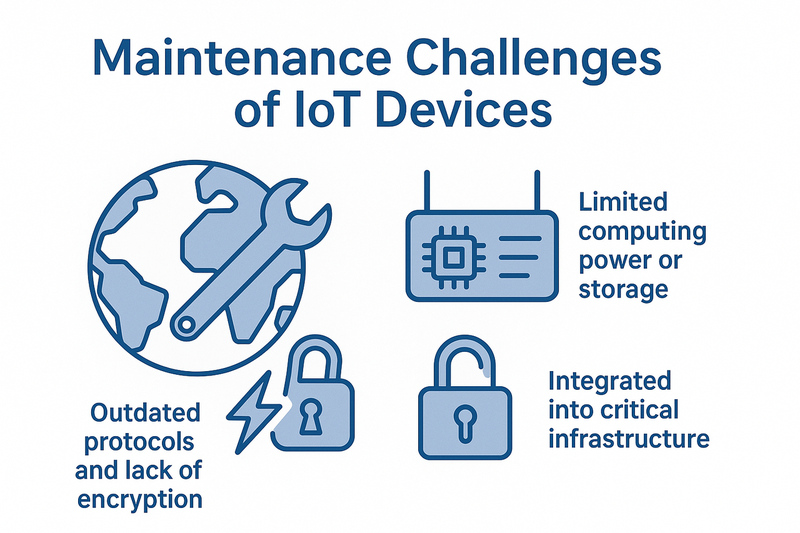
Maintaining IoT devices is often a significant challenge, as these devices are typically scattered across the globe and integrated into custom environments. Many of them have limited computing power or storage, making automatic updates difficult. In addition, outdated protocols and lack of encryption pose extra security risks. These devices are also frequently part of critical infrastructure, introducing further challenges for maintenance.
OTA Updates as a Solution
Over-the-Air updates (OTA updates or OTA patching) offer an automated distribution of firmware, patches, or new features directly to devices, regardless of their location. They often include built-in rollback mechanisms to quickly restore the previous state in case of a faulty update.
This brings significant benefits regarding the speed of the update cycle. Patches can be deployed to all devices within hours or days without requiring complex logistics. One of the most important use cases is the rapid response by manufacturers to security vulnerabilities in network devices, which must be closed as quickly as possible. Additionally, physical maintenance deployments can be avoided.
Must-Haves for OTA Software
When selecting appropriate OTA software, many criteria must be considered. From security to cross-system compatibility to operational features, the software should meet several key requirements:
- Security-by-Design: Security is built in from the start. This includes encrypted data transmission, access control, continuous security testing, and regular updates to the OTA infrastructure.
- Zero Trust Architecture: A security model that trusts no device or user by default – every communication and action is verified. This minimizes the risk of internal and external attacks.
- Certificate-Based Authentication: Only clearly identified and authorized devices should receive updates. Certificates ensure that foreign or compromised systems cannot join the update infrastructure.
- Protection from Supply Chain Risks: The entire update chain – from developer to build system to delivery – must be protected against tampering and unauthorized access. Digital signatures and secure update sources are essential.
- Resource-Efficient Design: A good OTA system works even on devices with minimal resources. It handles limited memory, processing power, and network capacity, making it ideal for embedded or edge devices.
- Staged Rollouts (Canary Releases): Updates are first deployed to a small, selected portion of the device fleet. After successful testing, the full rollout follows – a proven strategy to prevent widespread failures.
Conclusion
OTA updates are a crucial lever for securing the growing IoT infrastructure. They enable rapid and automated updates while significantly reducing the need for physical maintenance. To unlock their full potential, OTA updates should be equipped with modern security measures and a Zero Trust strategy. Together, these concepts provide robust protection – making Over-the-Air patching an essential pillar of secure operations.